Today, data security is more important than ever. Cyberattacks, data breaches, and online privacy threats make it essential to protect personal and corporate information. Encryption is one of the most effective methods for safeguarding this data. But what exactly is encryption, and how does it protect your data? In this article, you will learn the basic concepts of encryption and how to use it to keep your data secure.
What is Encryption and How Does It Work?
Encryption is a technique that makes information unreadable by using algorithms and keys to encrypt data, ensuring that only authorized individuals can access it. Encryption protects data from unauthorized access. For example, when you encrypt a message, it is converted into an encrypted text that can only be read using the correct key.
Best Practices for Encryption
Use Strong Algorithms: Opt for secure and widely accepted encryption algorithms like AES and RSA. These algorithms protect your data through complex mathematical operations.
Strong and Unique Passwords: The security of encryption keys depends on the complexity of the password used. Create complex and unique passwords.
Password Managers: Use password manager software to securely store and manage your passwords.
Two-Factor Authentication (2FA): Along with encryption, use 2FA to add an extra layer of security to access your accounts.
Regular Updates: Keep your encryption software and devices updated. Updates close known security vulnerabilities.
Encryption on Devices
- Mobile Devices: iOS and Android automatically encrypt data on the device. In case the device is lost or stolen, encrypted data is harder to access.
- Computers: Tools like BitLocker on Windows and FileVault on Mac can encrypt hard drives. These tools make it easy to encrypt your data with user-friendly interfaces.
Avoiding Encryption Mistakes
- Using Weak Passwords: Easy-to-guess passwords compromise the encryption process. Always use complex, long, and randomly generated passwords.
- Securing Keys: Do not store encryption keys in insecure environments. Losing the keys means losing access to encrypted data.
- Neglecting Updates: Keep security software and encryption algorithms up to date. New updates usually contain security enhancements.
Encryption Tools
- Disk Encryption: Tools like BitLocker (Windows) and FileVault (Mac) allow you to encrypt all data on your device.
- File and Folder Encryption: VeraCrypt is a popular tool used for encrypting specific files and folders.
- Communication Encryption: Tools like GnuPG can be used to encrypt communications such as emails. Applications like Signal and WhatsApp offer end-to-end encryption.
Data Privacy and Encryption
Encryption is critical for ensuring data privacy. It protects your sensitive information from unauthorized access and provides a strong defense against data breaches. End-to-end encryption, in particular, ensures that no one but the sender and receiver can read your data.
End-to-End Encryption
End-to-end encryption (E2EE) ensures that data can only be read by the sender and the receiver. This type of encryption prevents third parties, including service providers, from eavesdropping on your communications. Applications like Signal and WhatsApp use this technology to secure your messages and calls.

Understanding the Basics of Encryption
Encryption is the process of converting data into an unreadable form, known as “ciphertext,” using an algorithm and a key. This ensures that only those with the correct key can convert the data back into a readable form. The primary purpose of encryption is to protect the confidentiality of data and prevent unauthorized access.
There are two ways to encrypt data: symmetric and asymmetric encryption. Symmetric encryption uses the same key for both encryption and decryption. Asymmetric encryption, on the other hand, uses two different keys: a “public key” to encrypt the data and a “private key” to decrypt it. Both types of encryption are used to secure data.
Types of Encryption: Which One Is Right for You?
There are two main types of encryption: symmetric and asymmetric. Symmetric encryption is advantageous in terms of speed and simplicity, but it can pose a problem when it comes to securely sharing the key. Asymmetric encryption is more secure because it uses a public key for encryption and can only be decrypted with a private key. However, this method is more complex and slower.
The type of encryption you choose depends on the nature of the data and the usage scenario. For personal files, symmetric encryption may be suitable due to its speed and ease of use. However, for securing communications such as emails, asymmetric encryption may be a better choice.
Best Practices for Encrypting Your Personal Data
There are some fundamental practices to keep in mind when encrypting your data. First, choose a strong encryption algorithm. Widely accepted algorithms like AES (Advanced Encryption Standard) and RSA are reliable options. Additionally, use strong and unique passwords. Using a password manager can enhance the security of your passwords.
Second, enable two-factor authentication (2FA). This adds a second layer of verification to access your accounts and protects them even if your password is stolen. Lastly, enable encryption options on your devices. Most modern operating systems have built-in features to automatically encrypt data on your devices.
How to Apply Encryption on Your Devices
Most devices and operating systems offer built-in encryption tools to protect your data. For example, iOS and Android devices automatically encrypt your data using the device’s lock screen password. This ensures that your data remains secure even if your device is lost or stolen.
Windows users can use tools like BitLocker to encrypt their hard drives. Mac users can use FileVault to protect their data. These tools provide easy and effective ways to encrypt and safeguard your data.
Common Encryption Mistakes to Avoid
While encryption is an effective way to protect your data, it may not provide the desired security if implemented incorrectly. Common mistakes to avoid include using weak passwords, storing encryption keys insecurely, and neglecting updates. Make your passwords difficult to guess and use complex character combinations. Store your encryption keys in a secure environment and update your systems regularly.
Encrypting Data on Cloud Services: A Guide
Cloud services are widely used for storing and sharing data. However, to keep your data secure in the cloud, additional layers of encryption are necessary. Many cloud providers automatically encrypt your data, but it’s also important to take your own precautions. You can encrypt your data using your own encryption software before uploading it to the cloud and enable the encryption options provided by your cloud provider.
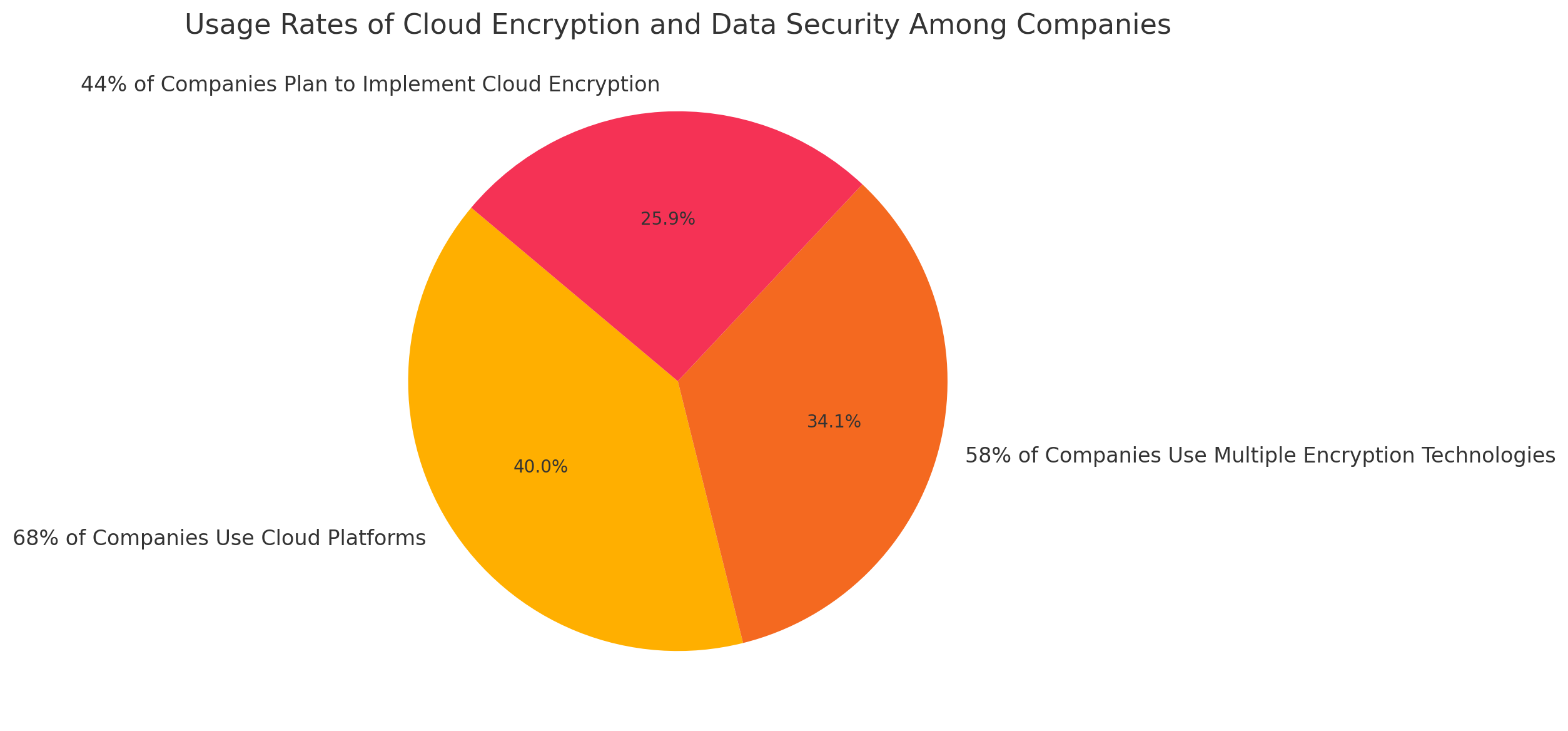
According to the data obtained from https://www.fortunebusinessinsights.com/, Cloud Encryption and Data Security Usage Rates of Companies are as follows:
With the growing demand for security solutions among large companies and SMEs, services that were once expensive have now become more economically viable, fitting into a company’s budget without draining its funds. For example, according to Encryption Consulting’s 2023 report, 68% of companies use cloud platforms to store sensitive data, 58% use multiple encryption technologies for data protection, and 44% plan to implement cloud encryption within the next two years. Additionally, according to Fortune Business Insights, the cloud encryption market, which was valued at $3.18 billion in 2023, is expected to reach $34.63 billion by 2032. This growth will occur with a staggering compound annual growth rate (CAGR) of 30.7% between 2024 and 2032.
Tools and Software for Easy Data Encryption
There are various tools and software available for encrypting your data. BitLocker (Windows) and FileVault (Mac) are built-in tools that can encrypt your entire disk. Additionally, third-party software like VeraCrypt can be used to encrypt disk partitions or files.
For file sharing or email transmission, PGP-based tools like GnuPG offer an effective solution for end-to-end encrypting your data. Messaging applications like Signal and WhatsApp also offer end-to-end encryption to protect your communication.
The Role of Encryption in Data Privacy
Encryption plays a crucial role in data privacy. By encrypting your data, you ensure that only authorized individuals can access it. This is necessary to protect both personal and corporate data confidentiality. Encryption provides a significant defense layer against data breaches and prevents sensitive information from falling into the wrong hands.
Ensuring Secure Communication with End-to-End Encryption
End-to-end encryption (E2EE) ensures that communication is readable only between the sender and the recipient. This means that even if your messages and data are intercepted by third parties, they remain unreadable. Applications like Signal and WhatsApp use end-to-end encryption to provide secure communication. This is an effective method to ensure the security of your messages and calls.
Encryption is one of the most effective ways to protect your data. Whether it’s personal or corporate data, encryption can help you keep your information secure. With strong encryption methods and proper practices, you can protect your data from unauthorized access and ensure online privacy. Remember, encrypting your data is just one step; you also need to keep your passwords strong, stay on top of updates, and adopt best practices for security.