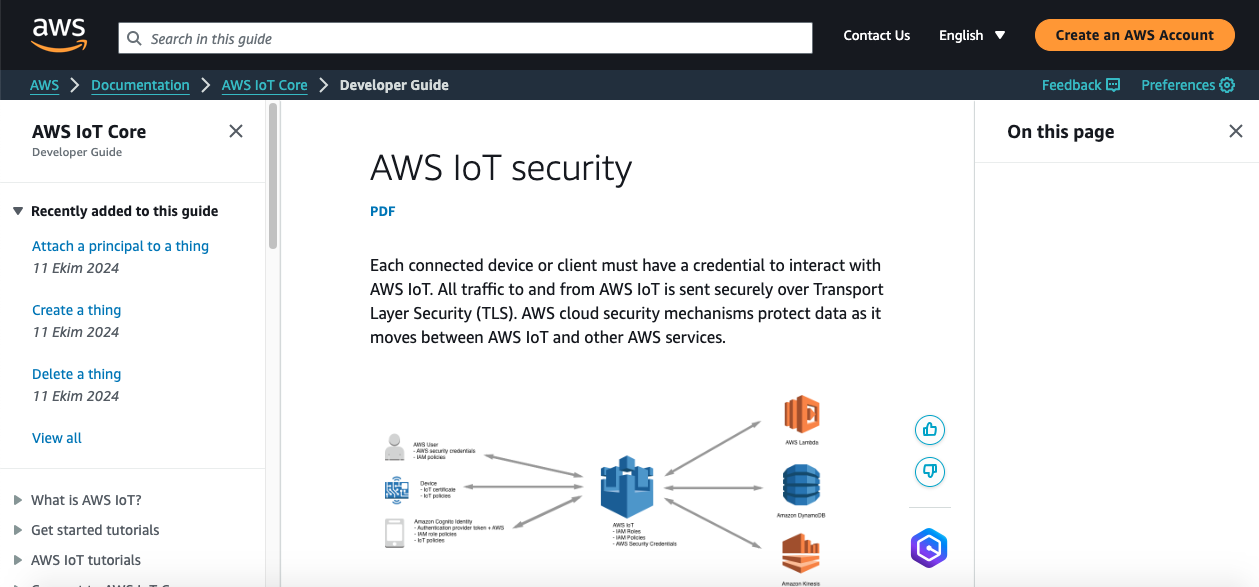
Today, Internet of Things (IoT) devices are widely used in many areas, from homes to industries. These devices facilitate users’ daily lives but also bring serious security risks. Ensuring the security of IoT devices is crucial for both data privacy and the integrity of systems. In this article, we will focus on the best practices to ensure IoT device security and examine how we can mitigate potential risks.
What Is IoT Security and Why Is It Important?
IoT security refers to the protection of internet-connected devices and the networks they are linked to from external threats. IoT devices can be vulnerable to cyberattacks during the process of collecting and transmitting data. These devices, which range from smart home systems to industrial machines, can cause serious harm to both individual and corporate users if their security is breached.
These devices often collect sensitive information, and unauthorized access to this data can lead to significant security issues. Especially when data is transmitted between devices without encryption, they become easy targets for attackers. For this reason, IoT security plays a critical role in protecting data privacy and ensuring that devices operate securely.
Basic Steps to Ensure IoT Device Security
There are fundamental steps that can be taken to enhance the security of IoT devices. First, it is crucial to change the default settings of the devices. Devices are typically provided by manufacturers with simple, easily guessable passwords. Users must replace these default passwords with more complex and strong ones.
Additionally, keeping the device software up-to-date is of great importance. Manufacturers periodically release updates to fix security vulnerabilities in devices. If these updates are not applied, the devices become vulnerable to attacks. Enabling automatic update options can help prevent this issue.
Another critical step is using secure communication protocols. Encrypting data transmitted from the device to the network is a key security measure to prevent unauthorized access to this data.
How to Detect Security Vulnerabilities in IoT Devices?
Identifying security vulnerabilities in IoT devices is essential for protecting these devices. Vulnerabilities are often caused by weak authentication, outdated software, or insecure connection protocols. To detect such vulnerabilities, regular security tests should be conducted. Penetration testing and dynamic security scans allow early detection of these vulnerabilities.
In addition, monitoring devices for abnormal behavior on the network and disabling them if necessary is an effective way to close security gaps. Attackers often aim to exploit weak points in IoT devices to infiltrate systems. Therefore, regular network monitoring and security audits play a critical role in ensuring the security of IoT devices.
The Dangers of Default Passwords and How to Avoid Them
Many IoT devices come with simple default passwords during installation, and if these passwords are not changed, they pose a significant security risk. Leaving default passwords unchanged can lead to the device being easily taken over. For this reason, users must change the default passwords during the initial setup to more complex and unique ones.
Moreover, using multi-factor authentication (MFA) whenever possible adds an extra layer of security by requiring two steps for device access, not just a password. This method is one of the most effective ways to prevent unauthorized access to devices.
How to Ensure Data Privacy in IoT Devices?
IoT devices collect personal information from users, and ensuring the security of this data is a major concern. Encrypting data both when stored on the device and during transmission is one of the primary ways to protect privacy. Especially in devices that collect sensitive data, industry-standard encryption methods should be used. Widely used algorithms like AES-256 provide strong security for data.
Additionally, managing data access permissions properly is essential. Ensuring that each user can only access the data they need is crucial for security. This is especially important for corporate devices handling large datasets.
How to Monitor and Protect IoT Devices on Your Network?
Monitoring the activity of IoT devices on the network is one of the most effective ways to detect security vulnerabilities. Many devices may reveal security breaches through abnormal increases in network traffic or unusual connection requests. Therefore, it is necessary to monitor the connections of IoT devices using network monitoring software and to detect abnormal activities.
In addition, keeping IoT devices on a separate network from critical systems is also an important step for security. By segmenting the network, IoT devices can be isolated from systems that process sensitive data, preventing the spread of risks in the event of a breach.
The Importance of Firmware Updates
Firmware updates play a critical role in ensuring the security of IoT devices. Manufacturers regularly release updates to fix security vulnerabilities discovered in devices over time. If these updates are not applied, the device becomes vulnerable to known security issues.
Firmware updates not only introduce new features but also include security patches. Therefore, it is essential to keep devices up-to-date at all times. Enabling automatic update options can help maintain the security of the devices without requiring manual intervention from users.
Keeping IoT Devices Safe in Smart Homes
IoT devices used in smart home systems offer great advantages for home security. However, neglecting the security of these devices can lead to weak defenses against cyberattacks. One of the most effective ways to keep IoT devices secure in smart homes is to ensure that each device has a unique password and that security protocols are properly applied.
Moreover, securing the networks to which the devices are connected and supporting them with tools like firewalls and VPNs provides an additional layer of protection. In smart home systems, monitoring network traffic and detecting abnormal activities are effective ways to enhance in-home security.
Measures Against IoT Botnet Attacks
IoT devices can be compromised by attackers and included in botnet networks. These attacks often result in large-scale distributed denial-of-service (DDoS) attacks. To protect IoT devices from such attacks, ensuring the security of the devices is essential.
The most effective measures against botnet attacks include using strong authentication methods, regularly updating software, and monitoring device network traffic. Additionally, limiting the amount of traffic generated by devices can help reduce the impact of large-scale attacks carried out by attackers using these devices.
The Role of Strong Authentication in IoT Devices
Strong authentication mechanisms play a crucial role in ensuring the security of IoT devices. Many devices come with weak passwords or default credentials, making it easy for attackers to gain access. Using strong authentication methods protects devices from such attacks.
Multi-factor authentication (MFA) is an effective method in this regard. Allowing users to access devices through both a password and an additional verification step prevents unauthorized entries. This method is particularly important for IoT devices that handle sensitive data.
What are the adoption rates of IoT security worldwide?
According to data from https://www.paloaltonetworks.com/:
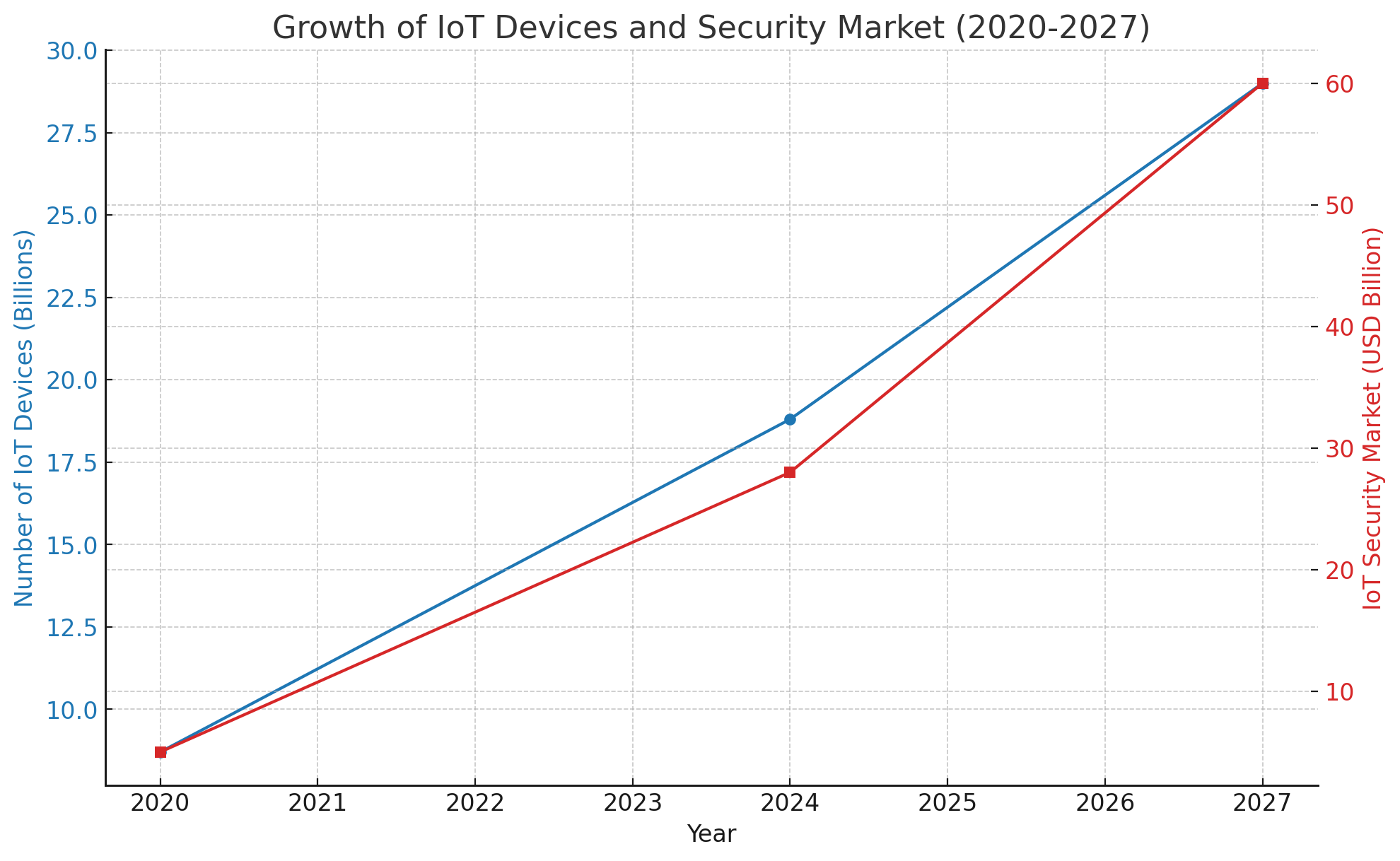
The rapid increase in the number of IoT devices has reached 18.8 billion globally as of 2024, and this number is expected to rise to 29 billion by 2027. This rapid growth has also led to a significant rise in security threats, and as a result, spending on IoT security has increased considerably. The IoT security market reached $28 billion in 2024, and it is projected to grow to $60 billion by 2027. However, security vulnerabilities still exist, particularly in devices such as smart TVs and routers, which underscores the need for more robust security measures.
Which brands use IoT Device Security?
Several well-known brands from various sectors are actively using IoT device security solutions to protect their networks and connected devices from cyber threats. These brands are implementing advanced security practices across different industries like healthcare, manufacturing, and retail. Here are some of the prominent brands using IoT security:
General Electric (GE): GE uses IoT security in its healthcare and industrial equipment to ensure the protection of critical infrastructure and sensitive data.
Siemens: Siemens integrates IoT security solutions into its industrial systems and smart factory technologies to ensure secure operations across its global facilities.
Amazon (AWS IoT): Amazon Web Services (AWS) offers IoT security for its cloud services, helping companies manage and secure their IoT devices at scale.
Tesla: Tesla uses IoT security in its connected cars and autonomous vehicle systems to prevent unauthorized access and protect user data.
Caterpillar: Caterpillar employs IoT security for its connected heavy machinery and equipment in industries like construction and mining to improve operational efficiency and secure its devices.
Microsoft (Azure IoT): Microsoft provides IoT security as part of its Azure IoT platform, which is widely used across multiple sectors, including retail, logistics, and smart cities.
These brands rely on a combination of software, hardware, and cloud-based IoT security solutions to safeguard their devices and data, emphasizing the critical importance of cybersecurity in the IoT ecosystem.
Ensuring the security of IoT devices is vital for both individuals and organizations to protect against cyber threats. Changing default passwords, applying software updates, using strong authentication methods, and monitoring the activity of devices on the network are essential steps for securing IoT devices. These security measures not only protect the devices themselves but also safeguard the entire network they are connected to, significantly reducing security risks.