In today’s digital world, ensuring the security of data has become more important than ever. With the rapid increase in cyberattacks and data breaches, protecting sensitive information has become a vital necessity. In this context, Advanced Encryption Standard (AES) 256-bit encryption stands out as a powerful and reliable data security solution. In this article, we will explore why AES-256 encryption is one of the best options for data security and how it meets the modern data protection needs.
Why is AES-256 Secure?
Unmatched Security Strength
AES-256 encryption is considered one of the strongest encryption methods available. The 256-bit key is used for both encryption and decryption processes. This means there are 2^256 possible key combinations. It is practically impossible for even the world’s most powerful supercomputers to try such a vast number of combinations. In fact, it is estimated that it would take billions of years with current technologies to break AES-256. This is one of the main reasons why AES-256 is nearly impervious to brute-force attacks, making it a highly secure option.
AES-256 encryption plays a critical role in modern data security practices and is essential for protecting data in today’s digital world. With advancing technology, threats such as cyber-attacks and data breaches are increasing rapidly. Therefore, using a strong and reliable encryption method is essential for protecting sensitive information. AES-256 encryption is one of the strongest encryption methods preferred to ensure data security at both individual and corporate level.
How Does AES-256 Protect Against Data Breaches?
Strong Defense Against Data Breaches
Even if a system is compromised, AES-256 encryption ensures that the stolen data remains inaccessible to malicious individuals. Even if there is a security vulnerability in your system, the encrypted data can only be decrypted by authorized users. This ensures that the data remains entirely meaningless and inaccessible to anyone who does not possess the encryption key. This feature is particularly crucial for protecting sensitive information such as financial data, personal information, or trade secrets.
Why Do Security Experts Prefer AES-256?
A Globally Trusted Encryption Method
AES-256 has earned the trust of governments, military organizations, and security professionals around the world due to its reliability and strength. Its use by the U.S. government to protect highly classified information, including top-secret data, demonstrates how reliable this encryption method is. Moreover, AES-256 has been extensively tested over the years by cybersecurity experts and has not encountered any major security vulnerabilities in practice. This has made it a standard in the field of security.
Prepared for Future Threats
As the power of today’s computers rapidly increases, it is anticipated that even more powerful technologies, such as quantum computers, will emerge in the future. These types of technologies could threaten some current encryption methods. However, AES-256 is highly resistant to these future threats. Especially when considering that quantum computers could pose a significant threat to traditional encryption methods, AES-256 is strong enough to withstand such next-generation attacks. Therefore, if you want to ensure the long-term security of your data, AES-256 is an ideal choice.
Is AES-256 Fast and Efficient for Everyday Use?
Fast and Efficient Encryption
While providing a high level of security, AES-256 also offers fast and efficient encryption. It can quickly encrypt and decrypt large amounts of data without causing significant performance loss. This is a crucial advantage for both businesses and users, as it allows for secure data protection while maintaining rapid processing speeds. Additionally, AES-256 works seamlessly across various platforms due to its compatibility with different devices, making it a convenient encryption method for both individuals and organizations.
Does AES-256 Comply with Global Data Protection Laws?
Compliance with Global Data Protection Laws
Businesses operating in the field of data security must comply with international regulations such as GDPR (General Data Protection Regulation) and HIPAA (Health Insurance Portability and Accountability Act). AES-256 is an excellent tool for ensuring compliance with these regulations. This encryption method, especially used to protect sensitive personal data, allows businesses to meet legal requirements and avoid penalties that may arise from data breaches.
How Does AES-256 Prevent Unauthorized Access?
Protection Against Unauthorized Access
AES-256 completely prevents unauthorized individuals from accessing the data. Only authorized individuals with the encryption key can decrypt the data. Therefore, AES-256 is especially preferred for protecting sensitive information such as financial transactions, communication data, and confidential documents. The symmetric encryption method used ensures that the same key is used for both encryption and decryption, further enhancing data security.
On Which Platforms is AES-256 Supported?
Versatile and Widely Supported
One of the most significant advantages of AES-256 is its widespread support across various platforms and devices. It can be used on devices such as laptops, smartphones, and cloud storage systems. This versatility allows both businesses and individuals to easily integrate AES-256 into their systems. Furthermore, many popular applications and services use AES-256 encryption as the default security standard. For example, major platforms like Google Cloud, AWS (Amazon Web Services), and WhatsApp prefer this encryption.
What are the global adoption rates of AES-256 encryption?
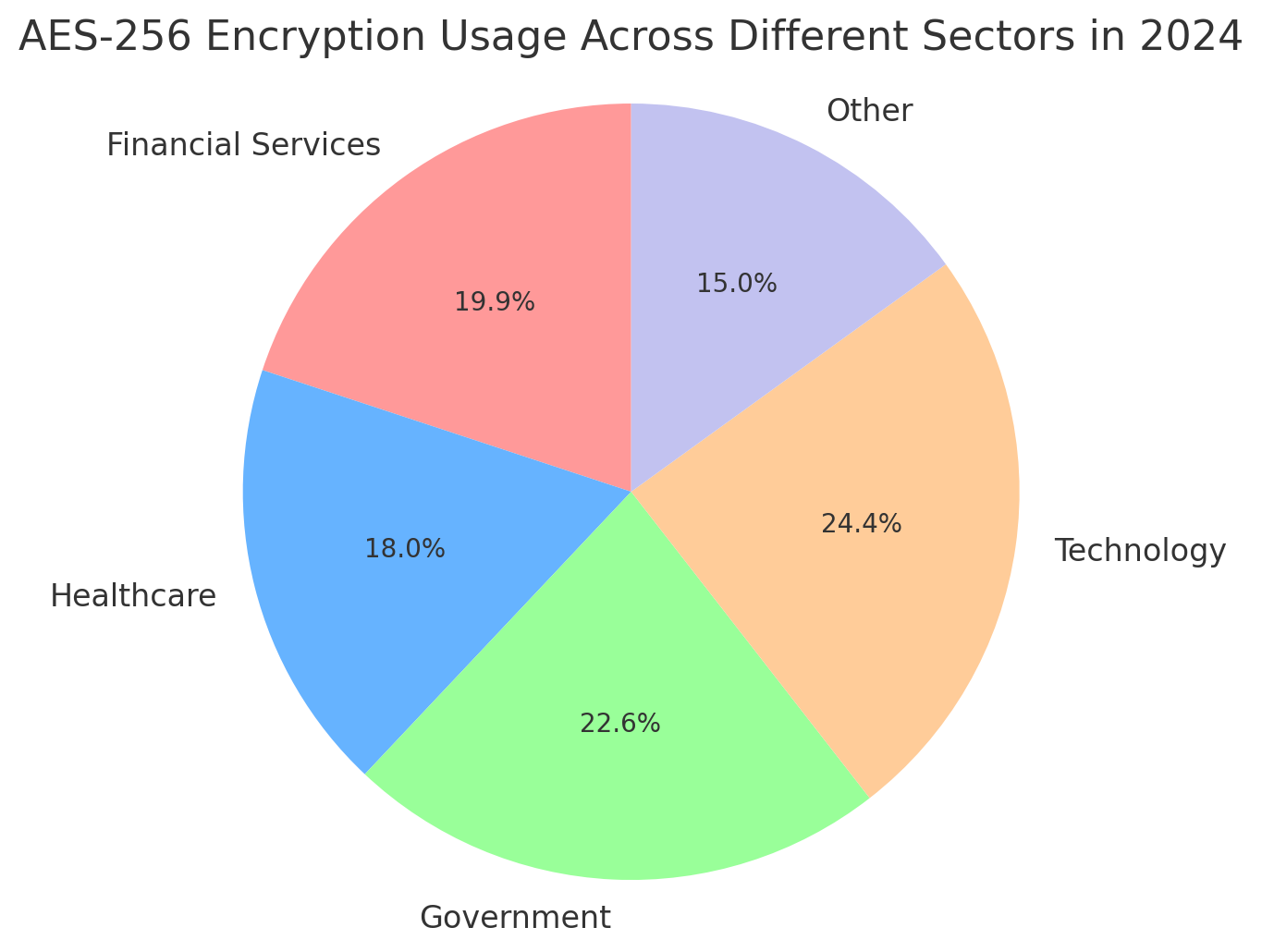
AES-256 encryption is widely used as one of the most trusted encryption standards worldwide in 2024. It is especially widely used in the financial, healthcare, government and technology sectors. Around 53% of data is protected with AES-256 in financial services, 48% in healthcare, 60% in government and 65% in technology. These high percentages indicate that AES-256 is preferred for its strong security features. This encryption method is widely used by large cloud service providers and other critical infrastructure, making it one of the most important tools for global data security.
Differences between AES-256 and Other Encryption Methods?
Prevalence of AES-256: AES-256 is a leader in both individual and corporate use. It is particularly used as the standard encryption method in cloud services (such as Google Cloud, Amazon Web Services, Microsoft Azure), messaging applications (like WhatsApp), and in military and government-level security applications. It is preferred for protecting data both at rest and in transit.
Comparison with AES-128: AES-256 is generally preferred over AES-128 due to its stronger security. However, AES-128 is chosen in scenarios where performance is critical, as it requires less processing power. Still, in sectors with high-security requirements, the adoption rate of AES-256 is much higher.
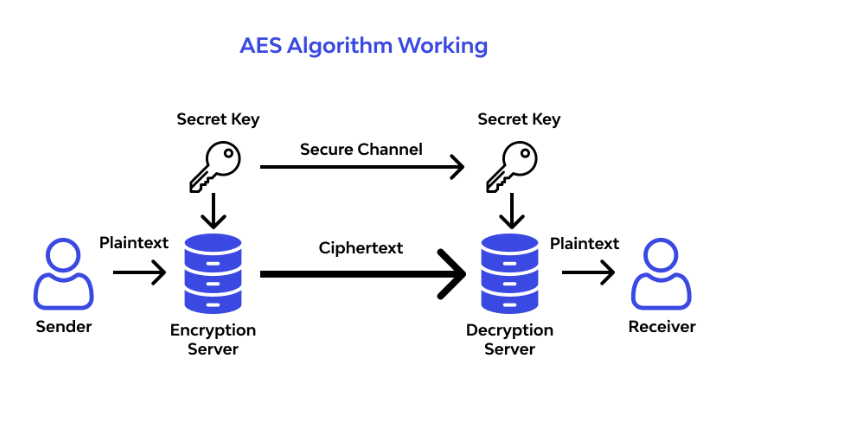
Comparison with RSA and Other Encryption Methods: Asymmetric encryption algorithms like RSA are typically used for key exchanges or digital signatures, whereas symmetric encryption algorithms like AES-256 are more effective for encrypting large amounts of data. Therefore, AES-256 is widely used in areas where data volume is significant. For example, in the financial sector, credit card information and sensitive financial data are often encrypted with AES-256. RSA, being more complex and requiring more processing power, has a more limited use.
AES-256 encryption provides unparalleled protection when it comes to data security. Its high resistance to cyberattacks and its compliance with global regulations make this encryption method one of the best choices for both individuals and businesses. AES-256 offers an excellent solution for ensuring not only the security of data against current threats but also for protecting it from future technological advances. If you want to keep your data secure and establish a robust digital infrastructure for the long term, choosing AES-256 is the right decision.











